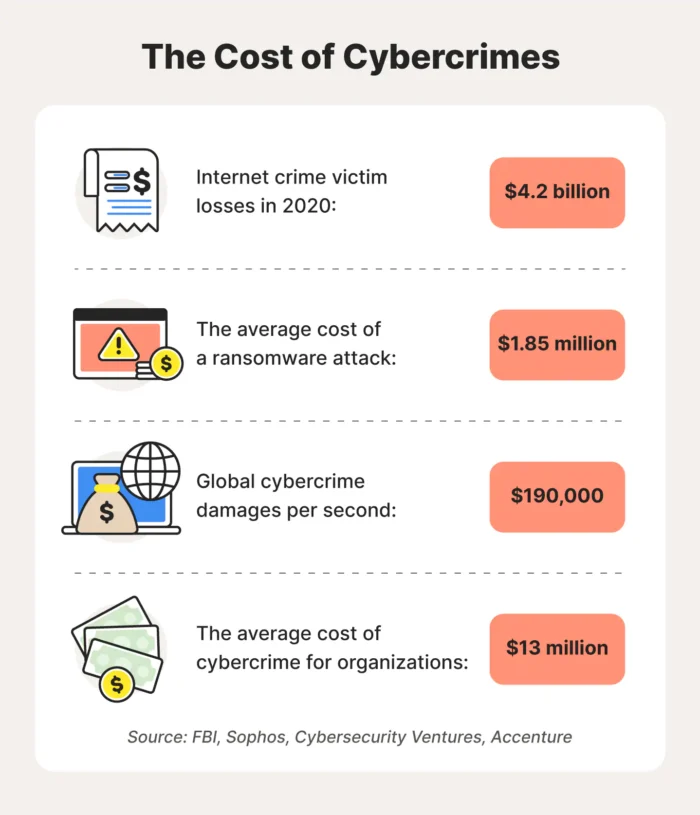
Cybersecurity has become increasingly important as the world becomes more interconnected and digitized. But the risks and costs of cybercrime continue to grow, as well, and the costs are staggering:
Against this threat, blockchain technology has been making waves in the world of cybersecurity for quite a few years now, and this innovative technology has the potential to revolutionize the way we approach online security—changing it for the better.
Here are some of the ways that we believe blockchain can be used to improve cybersecurity:
Immutable Records
To transact commerce (as an organization or individual) or operate government in a digital ecosystem requires legally enforceable digital signatures to prove agreement and intent.
Blockchain technology has an ability for the creation of immutable records, providing a secure, auditable trail of all transactions. All records and changes within a document are tracked and cannot be changed, providing important chain-of-custody audit capabilities for courts and ensuring peace of mind to its users. This also makes it ideal for use in financial transactions, real estate agreements and other high-value exchanges, where a record of every step is essential for ensuring the integrity of the process.
Secure Authentication
One of the main issues in cybersecurity is the vulnerability of traditional authentication methods such as passwords. Passwords can be easily hacked or stolen, leaving sensitive information vulnerable to attack. This can be a threat to businesses, especially those who store their users personal information. Blockchain technology can be used to provide secure authentication through the use of public-private key cryptography.
“The public key can help in encrypting a message before sending it to the concerned recipient,” explains 101 Blockchains. “When the recipient gets the message, they can use their private key for decrypting the message. It is essential to remember that only the recipient knows about the private key. Therefore, the applications of public key cryptography ensure that the valuable information of users is not tampered with in transit.”
Decentralization
Unliked centralized databases—which can be breached at unsecure endpoints (users and devices) or even at MSPs hosting them, giving attackers complete control once they gain central access—blockchain technology distributes data across geographically separate nodes. By decentralizing data storage, blockchain effectively prevents any one endpoint (even if compromised) from gaining control of the full data set.
This distributed nature so defeats any attack seeking to breach a system and holistically encrypt the data files stored therein: A single endpoint node might be breached and its files held for ransom, but the larger data set cannot be controlled by any one endpoint (or central authority) and so attackers cannot capture the full data set for encryption, ransom, and shutting down the network.
Further, with private, permissioned blockchains, each endpoint node (or user) has a unique encryption key to access and write to the distributed ledger. If any one of those endpoints is successfully attacked (presumedly compromising their access key), the private blockchain can simply remove distributed ledger access for that compromised key, issue the endpoint a new key, and allow that endpoint to quickly regain distributed ledger access (effectively as a new endpoint).
This unique recovery process effectively maroons any ransomware on the endpoint it attacked—ending its access and threat—while allowing the endpoint to re-engage the larger data set: With a new key and without needing to pay any ransom to the attackers for restored access.
Identity Verification
Identity verification is another area where blockchain can be used to enhance cybersecurity. It ensures that the individual claiming a particular identity is actually who they say they are. It is a very important aspect of digital security, especially as identity theft “frequency has sky-rockets in the past few years,” according to the National Council on Identity Theft Protection. “Nearly half of all U.S. citizens became a victim of some form of identity theft in 2020.”
With blockchain, users can have greater control over their personal information, allowing them to manage their digital identities more securely. This makes it more difficult for hackers to steal personal information or create fake identities.
ZorroSign’s Data Security Platform Built on Blockchain
As the world becomes more digitized and interconnected, the importance of cybersecurity will only continue to grow, and blockchain is poised to play a crucial role in ensuring that our digital world remains safe and secure.
ZorroSign’s data security platform was built on blockchain, delivering digital signatures, identity-as-a-service (IDaaS), patented fraud detection, user authentication, document validation, and document management all based on blockchain technologies.
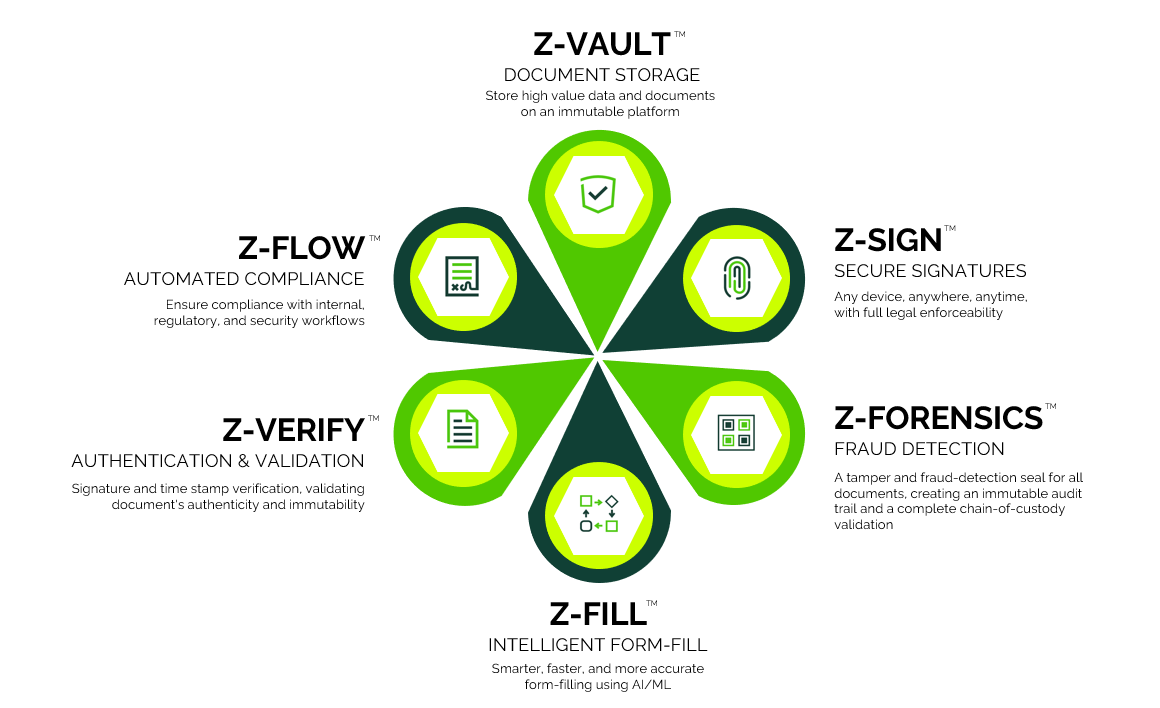
ZorroSign is a strong addition to any organization’s security stack and brings the cybersecurity capabilities of blockchain to digital signatures and transactional documentation.
To learn more, visit our platform page or contact us to start a free 14 day trial. When the security of your digital data and documents is on the line, block it down!