It is no secret that cybercrime has skyrocketed within the last few years, in fact, cybercrime in the U.S. jumped by 55%. This increased risk drives a greater need for privacy and security, especially within IT companies and departments responsible for digital data and cybersecurity.
ZorroSign can help your IT company or department combat the elevated security risks with our digital transaction platform, built on blockchain architecture, and calibrate your company and customers for success!
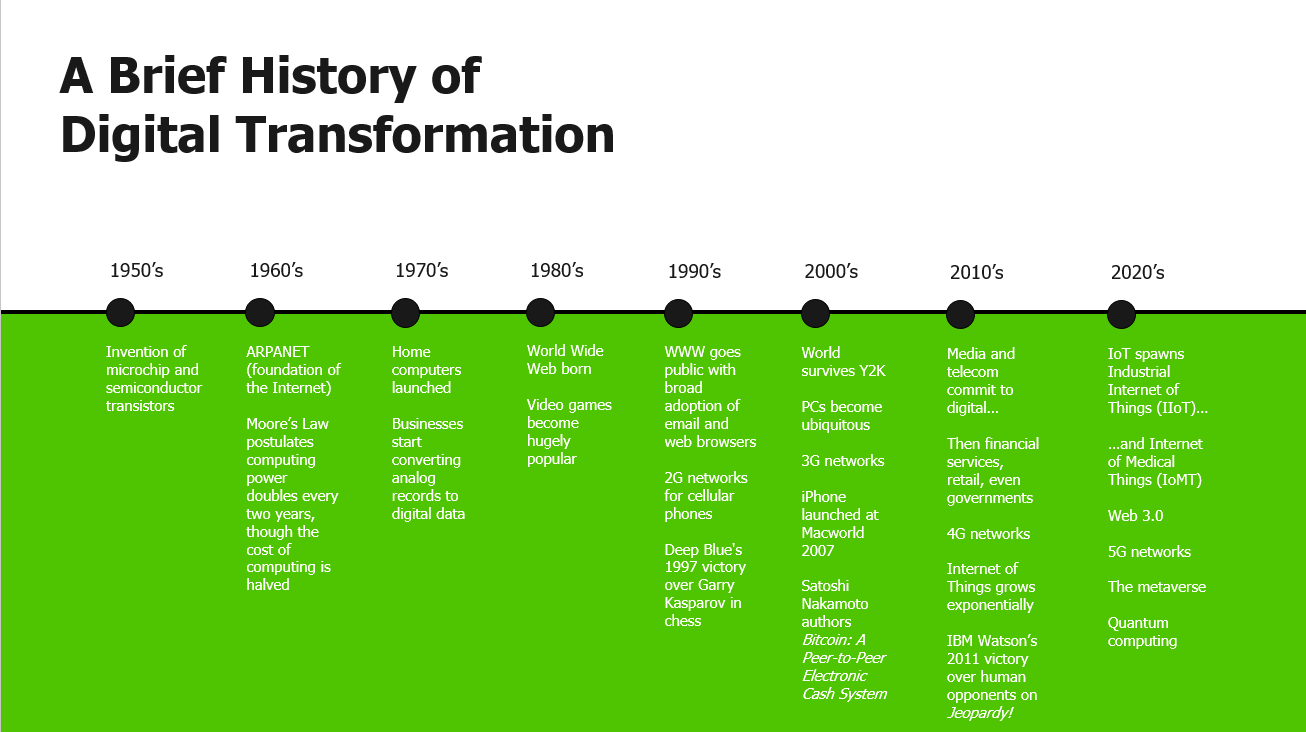
Blockchain Architecture For Elevated Security
ZorroSign is the only company that offers a multi-blockchain platform to secure, track, and manage your digital signatures, transactions, and documentation.
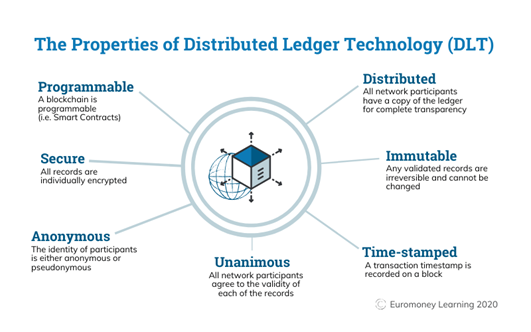
By using distributed ledger technologies—originally built on Hyperledger Fabric and recently expanded to include the Provenance Blockchain—ZorroSign provides superior privacy and security, offering peace of mind for your company’s and customers’ digital transactions, while preventing fraud and ensuring regulatory compliance.
How does this blockchain architecture contribute to ZorroSign being the best platform for IT companies?
Blockchain provides structural layers of protection from cybercrime, like ransomware, malware, or phishing attacks: First, by decentralizing the data set itself (preventing any one breach to access the entire data set); and second, by giving endpoints (or nodes) a quick path to recovery, even if they are themselves breached or their access ransomed.
Unlike centralized databases—which can be breached at unsecure endpoints (users and devices) or even at managed service providers (MSPs) hosting them—giving attackers complete control once they gain central access, blockchain technology distributes data physically across separate nodes. By decentralizing data storage, blockchain effectively prevents any one endpoint (even if compromised) from gaining control of the full data set.
This distributed nature so defeats any attack seeking to breach a system and holistically encrypts the data files stored inside: A single endpoint node might be breached, and its files held for ransom, but the larger data set cannot be controlled by any one endpoint (or central authority) and so attackers cannot capture the full data set for encryption, ransom, and shutting down the network.
ZorroSign is a strong addition to your security stack, and brings the cybersecurity capabilities of blockchain to your company’s and customers’ digital signatures and transactional documentation.
Z-Forensics Token
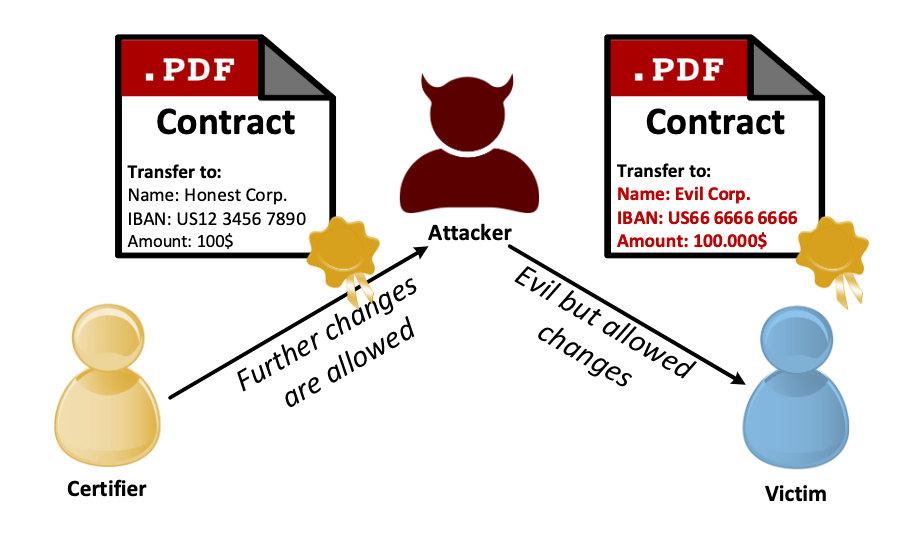
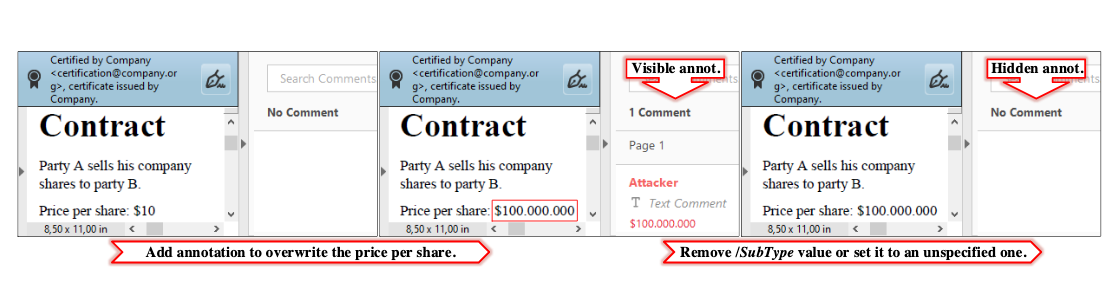
ZorroSign has further elevated our security through our patented fraud detection technology we call the Z-Forensics token.
This unique digital solution that can:
- Prove that the individual who is performing the action to sign the document is who they claim to be (verification);
- Apply a digital equivalent of a wet-ink signature to the document (legal intent); and,
- Prove the authenticity of the printed copy or digital version of an electronically signed document, its content, attachments, and the signatures on it (authenticity).
Unlike any other digital signature solution, ZorroSign seals all your documents with our Z-Forensics token—capturing the complete audit trail and accompanying attachments and signature workflow. The token is encrypted and contains all the details about the transaction: Time stamps, user authentication, documents and attachments.
Your IT company or department gains peace of mind when you Z-Sign!
Cloud Configuration
On top of providing the security that your company and customers need, ZorroSign’s software-as-a-service (SaaS) model can be deployed in various cloud configurations, making it seamless to integrate into your existing platform.
Our multi-chain blockchain platform can be deployed in a public, private, hybrid, or on-premise cloud:
- Our standard deployment is on Amazon Web Services (AWS) public cloud computing network
- In our private cloud configuration, all your data and the ZorroSign application run in a private and secure cloud network dedicated to your organization
- In a hybrid cloud configuration, your data can be stored on either ZorroSign data centers or in the private cloud, while the ZorroSign platform and applications run on their standard public cloud configurations
- On-premise deployments require your department to manage and maintain your own data centers, but gain the benefits of unlimited API calls and total control over identity access management (IAM), data privacy and security, and data integrity processes
Your IT company or department can scale and deliver data privacy and security aligned to your existing deployment architecture—as public, private, or hybrid as it may be!
To learn more about how ZorroSign helps IT companies and departments elevate your data privacy and security, please contact us or start your 14-day Free Trial today!