Block it down! Now, you can count on regulatory compliance and the immutability of your signed documents within your stored data and workflow records on ZorroSign’s blockchain.
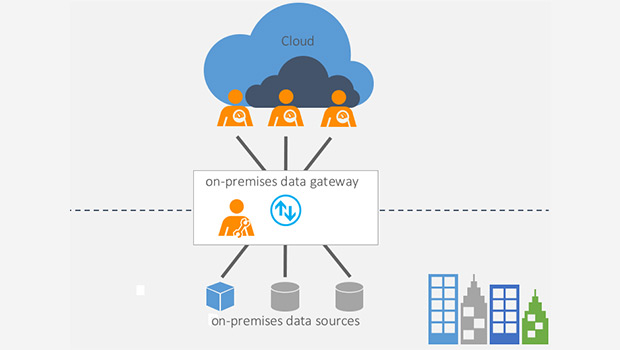
Z-Vault enables ZorroSign platform users to store, structure, organize and search documents in folders and subfolders natively, with the peace of mind that comes from superior privacy and security.
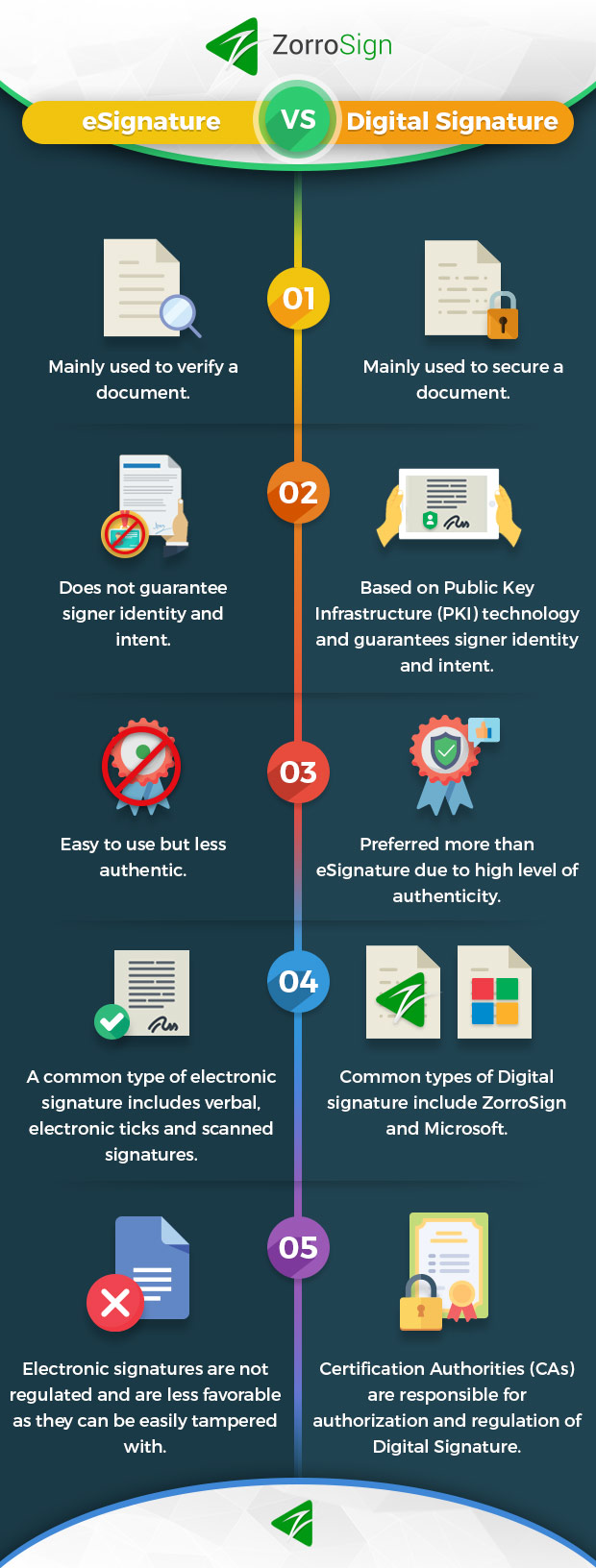
Digital Signatures on Blockchain
Since 2000, several technologies have come to market to deliver digital signatures, but when a distributed ledger technology—or DLT, such as blockchain—is used for digital signatures, signers gain the unique advantages of:
- Privacy — with a private blockchain, only participants to the transaction can see details of the transaction, and those participants share equal access to such details
- Immutability — all records and changes are tracked and cannot be changed, providing important chain-of-custody audit capabilities for courts
- Security — all records are individually encrypted and distributed for better protection from phishing and ransomware attacks
ZorroSign was built from the ground up on Hyperledger Fabric to deliver digital signatures with the superior privacy and security of blockchain. And we recently announced a partnership with Provence Blockchain to add their DLT to our architecture as well, effectively becoming a multi-chain blockchain platform.
Z-Vault for Better Contract Lifecycle Management
Contract lifecycle management, or CLM, spans the entire process of generating contracts, the workflows of approving and negotiating changes to contracts, the signing (or executing) of the contracts, storing and archiving the executed contracts, plus tracking and audit trails to retrieve contracts and review their lifecycle of approvals, iterations, and signatures.
If contracts are critical to your business or organization, then a secure, reliable solution for managing the contract life cycle is imperative.
Key functionality to look for when assessing CLM solutions include visibility (a dashboard or overview of where individual contracts are in the life cycle), integration with communications and storage systems, automation (as few contracts start from scratch—most are iterations of previously created agreements), and of course change tracking to readily see how contracts changed during negotiations and what final version was executed by all parties.
ZorroSign’s platform unites and uniquely delivers:
- Digital signatures via Z-Sign to quickly execute legally binding contracts
- Patented Z-Forensics token to prevent fraud and tampering
- Z-Flow workflow automation to quickly build templates and approval chains
- Z-Fill leveraging ZorroSign’s artificially intelligent, machine-learning engine
- Z-Verify to know exactly who signed what and when, with full validation of every document’s authenticity and immutability
- Z-Vault to securely store contract and transaction records immutably on blockchain
ZorroSign’s platform can be accessed via PCs and mobile devices, allowing your legal department, operations and procurement teams, and sales teams to efficiently generate, negotiate, communicate, and sign agreements. And with our Z-Vault, contracts reside on an immutable DMS where they can be saved, searched for, and managed easily from a single, intuitive user interface.
Z-Vault Benefits
- Superior privacy and security to PKI-based solutions using a centralized database
- The latest privacy and security technologies, delivering powerful encryption safeguards
- Secure, yet intuitively navigable and easily accessible (for authorized users) platform
- Ability to share and review eSign and architectural drawings, adding your own comments
- Time savings with access to specific folders and documents in seconds, no loss of records
ZorroSign Privacy & Security Compliance
Our combination of security architecture and data privacy functionality ensure your compliance across many international standards for privacy and security, including:
- Canada: The Personal Information Protection and Electronic Documents Act (PIPEDA)
- Canada: The Uniform Electronic Commerce Act (UECA)
- EU: Data Protection Regulation (GDPR) for data privacy and security
- EU: The electronic IDentification, Authentication and trust Services (eIDAS) regulation
- India: The Information Technology Act 2000 (IT Act of India)
- International Standard on Assurance Engagements (ISAE) No. 3402, Type II audited
- International Organization for Standardization (ISO) 27001 certified
- PDF Advanced Electronic Signatures (PAdES) is a set of restrictions and extensions to PDF and ISO 32000-1
- UAE: Federal Law No. 1 of 2006 regarding Electronic Transactions and E-Commerce granting electronic signatures legal force and effect
- USA: American Institute of Certified Public Accountants (AICPA) SOC 2 Type I audit
- USA: California Consumer Privacy Act (CCPA)
- USA: Department of Commerce’s National Institute of Standards and Technology (NIST) encryption standards
- USA: The Digital Millennium Copyright Act (DMCA)
- USA: The Electronic Signatures in Global and National Commerce Act (E-Sign Act)
- USA: FDA Title 21 of the Code of Federal Regulations; Electronic Records; Electronic Signatures
- USA: The Health Insurance Portability and Accountability Act (HIPAA)
- USA: The Uniform Electronic Transactions Act (UETA)
To learn more about Z-Vault and how ZorroSign can help you securely store contracts, data, and documents on blockchain, contact us today or start your 14-day Free Trial subscription!