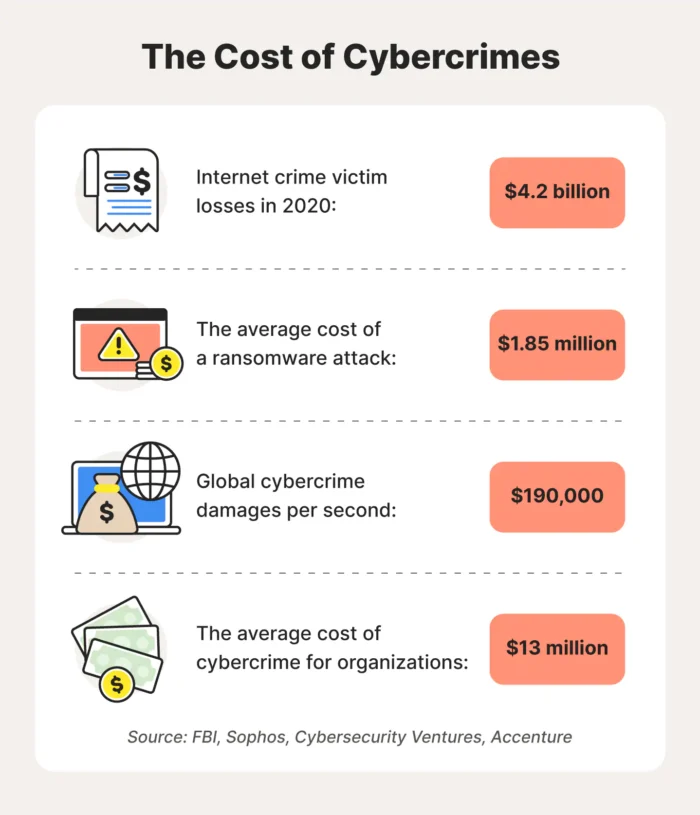
A recent Crowdstrike blog argues how “like so many legacy technologies, legacy data loss prevention (DLP) tools fail to deliver the protection today’s organizations need.”
Crowdstrike notes that with rising attacks, new attack vectors, and higher cost data breaches, organizations are desperate for a modern alternative to traditional cybersecurity solutions, where (as the blog summarizes):
- Unstructured data on endpoints is at great risk of misuse or breach
- More than a third of data loss prevention deployments fail
- Your data is too complex for legacy data loss prevention tools
- Legacy data loss prevention tools lack visibility into real-world data flows, and so lack context to stop breaches
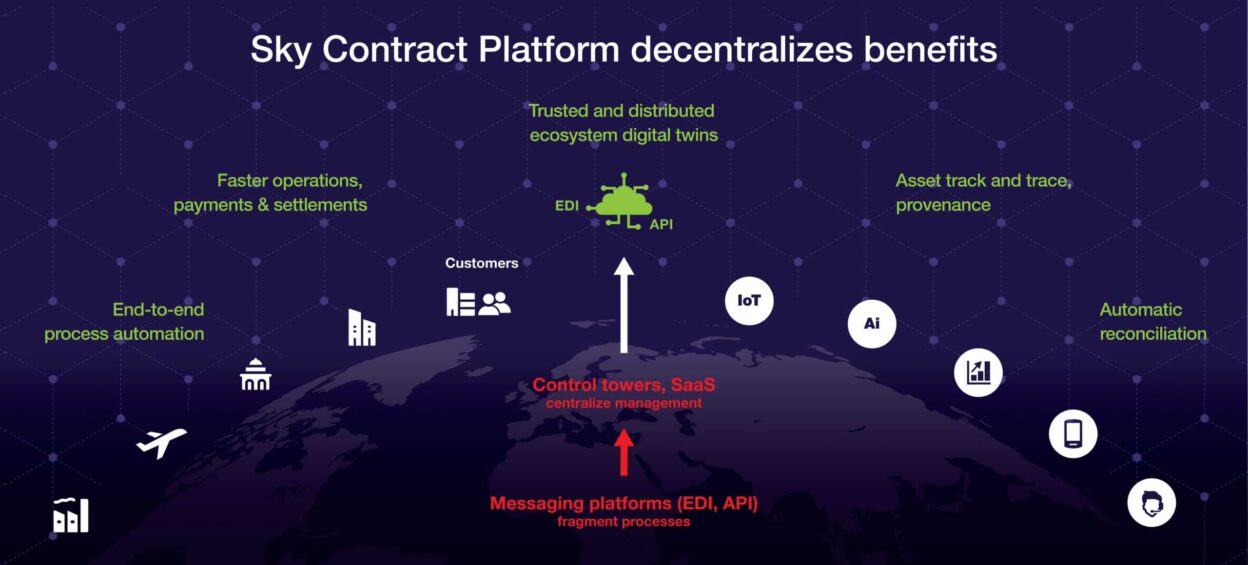
While I agree with all of Crowdstrike’s arguments, I believe blockchain technology improves cybersecurity and propose that storing your data on blockchain is a necessary leap forward in security versus legacy technologies.
Why is it vital that your organization moves to blockchain-based data storage? Four key reasons:
- Immutable Records
One of the main benefits of blockchain technology is its ability to provide secure and tamper-proof record keeping, as the use of cryptography and peer-consensus mechanisms ensures that once data is recorded on the blockchain, it is extremely difficult to alter or delete. This immutability and transparency provide important chain-of-custody audit capabilities for courts and ensure peace of mind to users. Such security also makes blockchains ideal for use in financial transactions, real estate agreements and other high-value exchanges, where a record of every step is essential for ensuring the integrity of the process.
- Secure Authentication
One of the main issues in cybersecurity is the vulnerability of traditional authentication methods such as passwords. Passwords can be easily hacked or stolen, leaving sensitive information vulnerable to attack. This can be a threat to businesses, especially those who store their users’ personal information. Blockchain technology can provide secure authentication through the use of public-private key cryptography, eliminating passwords from the process.
- Decentralization
Unliked centralized databases which can be breached at unsecure endpoints (users and devices)—or even at MSPs hosting them—giving attackers complete control once they gain central access, blockchain technology distributes data across geographically separate nodes.
The decentralized nature of blockchains ensures that there is no single point of failure, which also means that hackers cannot easily compromise the system. By decentralizing data storage, blockchain effectively prevents any one endpoint (even if compromised) from gaining control of the full data set.
This distributed nature defeats those attacks seeking to breach a system and holistically encrypt the data files stored therein. For example, breaching a single endpoint node and attempting to hold data “for ransom” fails, as the larger data set cannot be controlled by any one endpoint (or central authority) and so attackers cannot capture the full data set for encryption, ransom, or shutting down the network.
Further, with private, permissioned blockchains, each endpoint node (or user) has a unique encryption key to access and write to the distributed ledger. If any one of those endpoints is successfully attacked (presumedly compromising their access key), the private blockchain can simply remove distributed ledger access for that compromised key, issue the endpoint a new key, and allow that endpoint to quickly regain distributed ledger access (effectively as a new endpoint).
This unique recovery process effectively maroons any ransomware on the endpoint it attacked—ending its access and threat—while allowing the endpoint to re-engage the larger data set: With a new key and without needing to pay any ransom to the attackers for restored access.
- Identity Verification
Identity verification is another area where blockchain can be used to enhance cybersecurity. It ensures that the individual claiming a particular identity is actually who they say they are. With blockchain, users can have greater control over their personal information, allowing them to manage their digital identities more securely. This makes it more difficult for hackers to steal personal information or create fake identities.
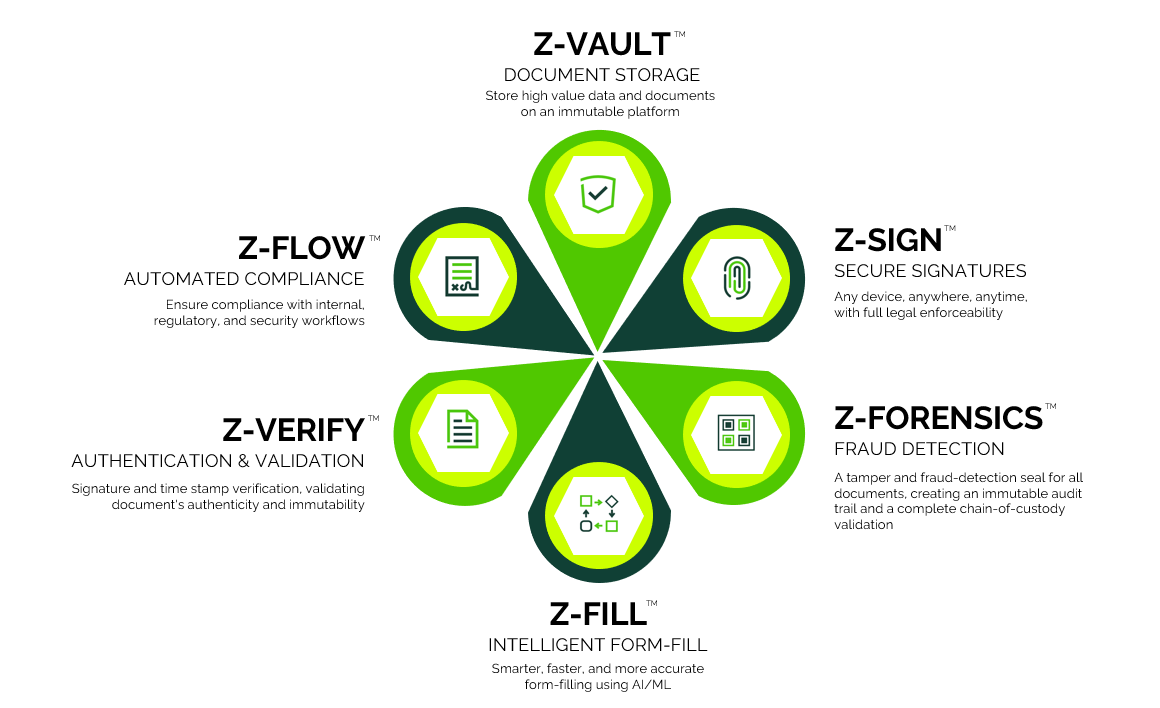
ZorroSign’s Data Security Platform Built on Blockchain
As the world becomes more digitized and interconnected, the importance of cybersecurity will only continue to grow, and blockchain storage will play a crucial role in ensuring that our digital world remains safe and secure.
ZorroSign was built from the ground up on Hyperledger Fabric to deliver digital signatures with the superior privacy and security of blockchain. We recently announced our advanced integration with Provence Blockchain, adding their DLT to our architecture as well.
Our Z-Vault® enables ZorroSign users to store, structure, organize and search documents in folders and subfolders natively with the peace of mind that comes from blockchain-based data privacy and security—leaving legacy technologies behind for good.
ZorroSign’s platform can be accessed via PCs and mobile devices, allowing your staff to efficiently generate, negotiate, communicate, and sign agreements. And with Z-Vault, contracts reside on an immutable document management system where they can be saved, searched for, and easily managed from a single, intuitive user interface.
Z-Vault Benefits for Your Organization
- Superior privacy and security to PKI-based solutions using a centralized database
- The latest privacy and security technologies, delivering powerful encryption safeguards
- Secure, yet intuitively navigable and easily accessible (for authorized users) platform
- Ability to share and review Z-Sign and architectural drawings, adding your own comments
Save time with access to specific folders and documents in seconds, no loss of records
I believe blockchain-based data storage is critical to improving cybersecurity, and I invite you to learn more about Z-Vault to securely store contracts, data, and documents on blockchain instead of legacy technologies.
Learn more about Z-Vault or connect with me on LinkedIn to start a conversation today!